Page 12 - The Indian EYE 051322
P. 12
OPINION MAY 13, 2022 | The Indian Eye 12
Russia–Ukraine Conflict and
Geopolitics of Data Routing
Russia’s special military operations in Ukraine brings to the foreground the geopolitics of data routing and the manner in
which states use data routing in contested areas to assert their power
KRUTIKA PATIL
n the aftermath of the 2014 Rus-
so-Ukrainian conflict, Russia
Igained control over the Crime-
an internet network, as well as that
of the Donbas region. Through data
protection laws and various other
measures, Russia gradually created a
Sovereign Internet/RuNet that gave
it complete control of all Internet
Transit Points in that region through
which data packets flow in the net-
work. Even before Russian troops
set foot in Donbas in the current
conflict, Russia had complete control
over the region’s internet network.
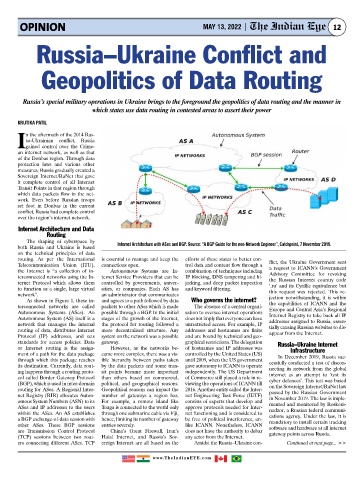
Internet Architecture and Data
Routing
The shaping of cyberspace by
both Russia and Ukraine is based Internet Architecture with ASes and BGP. Source: “A BGP Guide for the non-Network Engineer”, Catchpoint, 7 November 2019.
on the technical principles of data
routing. As per the International is essential to manage and keep the efforts of these states to better con- flict, the Ukraine Government sent
Telecommunication Union (ITU), connections open. trol data and content flow through a a request to ICANN’s Government
the Internet is “a collection of in- Autonomous Systems are In- combination of techniques including Advisory Committee for revoking
terconnected networks using the In- ternet Service Providers that can be IP blocking, DNS tampering and hi- the Russian Internet country code
ternet Protocol which allows them controlled by governments, univer- jacking, and deep packet inspection ‘.ru’ and its Cyrillic equivalence but
to function as a single, large virtual sities, or companies. Each AS has and keyword filtering. this request was rejected. This re-
network”. an administrator that communicates jection notwithstanding, it is within
As shown in Figure 1, these in- and agrees to a path followed by data Who governs the internet?
terconnected networks are called packets to other ASes which is made The absence of a central organi- the capabilities of ICANN and the
Europe and Central Asia’s Regional
Autonomous Systems (ASes). An possible through a BGP. In the initial sation to oversee internet operations Internet Registry to take back all IP
Autonomous System (AS) itself is a stages of the growth of the internet, does not imply that everyone can have addresses assigned to Russia, essen-
network that manages the internal the protocol for routing followed a unrestricted access. For example, IP tially causing Russian websites to dis-
routing of data, distributes Internet more decentralised structure. Any addresses and hostnames are finite appear from the Internet.
Protocol (IP) addresses, and sets system on the network was a possible and are bound by technical and geo-
standards for access policies. Data gateway. graphical restrictions. The delegation Russia–Ukraine Internet
or Internet routing is the assign- However, as the networks be- of hostnames and IP addresses was Infrastructure
ment of a path for the data package came more complex, there was a vis- controlled by the United States (US) In December 2019, Russia suc-
through which this package reaches ible hierarchy between paths taken until 2009, when the US government cessfully conducted a test of discon-
its destination. Currently, data rout- by the data packets and some tran- gave autonomy to ICANN to operate necting its network from the global
ing happens through a routing proto- sit points became more important independently. The US Department internet as an attempt to ‘test its
col called Border Gateway Protocol than others based on commercial, of Commerce still played a role in re- cyber defences’. This test was based
(BGP), which is used in inter-domain political, and geographical reasons. viewing the operations of ICANN till on the Sovereign Internet/RuNet law
routing for ASes. A Regional Inter- Geopolitical reasons can impact the 2016. Another entity called the Inter- passed by the Russian Government
net Registry (RIR) allocates Auton- number of gateways a region has. net Engineering Task Force (IETF) in November 2019. The law is imple-
omous System Numbers (ASN) to its For example, a remote island like consists of experts that develop and mented and monitored by Roskom-
ASes and IP addresses to the users Tonga is connected to the world only approve protocols needed for Inter- nadzor, a Russian federal communi-
within the ASes. An AS establishes through one submarine cable via Fiji, net functioning and is considered to cations agency. Under the law, it is
a BGP exchange-of-data session with hence, limiting its number of gateway be free of political interference, un- mandatory to install certain tracking
other ASes. These BGP sessions entries severely. like ICANN. Nonetheless, ICANN software and hardware at all internet
are Transmission Control Protocol China’s Great Firewall, Iran’s does not have the authority to debar gateway points across Russia.
(TCP) sessions between two rout- Halal Internet, and Russia’s Sov- any actor from the Internet.
ers connecting different ASes. TCP ereign Internet are all based on the Amidst the Russia–Ukraine con- Continued at next page... >>
www.TheIndianEYE.com